Use our free, easy-to-follow questionnaire to determine how close your organisation is to meeting all the Digital Operational Resilience Act (DORA) requirements.
Once completed, we’ll send you a free report outlining how prepared you are for DORA. You can use our output to create an action plan to achieve compliance.
If you need further support in setting up an action plan, or need advice about the requirements, our team of cyber experts can work with you on a roadmap to compliance.
How it works:
- Register with your company email
- Receive log in details via email
- Complete questionnaire (2-4 hours depending on organisation)
- Receive free report
- Plan your next steps with our DORA expert
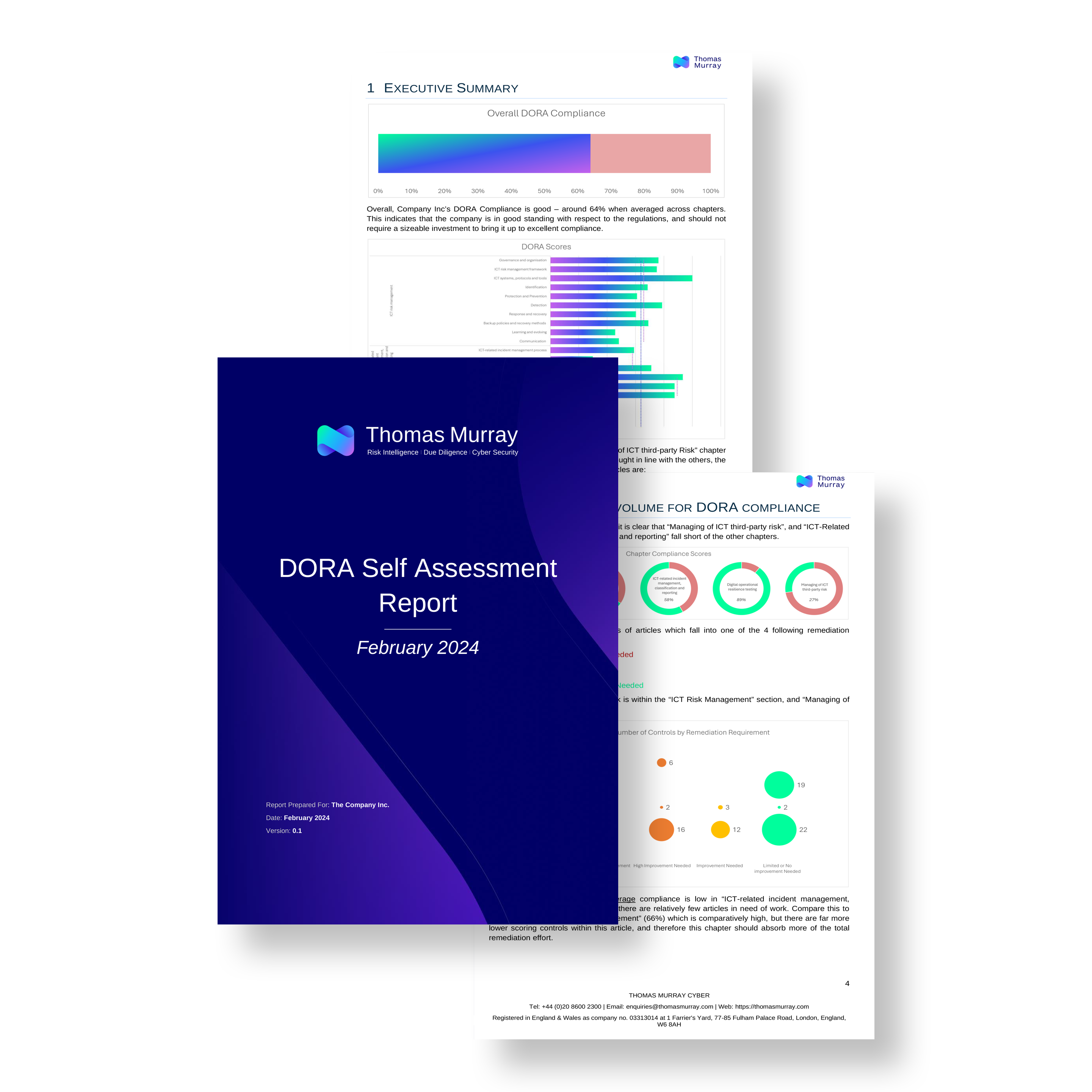
See an example of the report you will receive after submitting the assessment here.
Request your DORA Compliance Progress Check


Executive Readiness for DORA Workshops
With a deadline of January 2025 to be fully compliant with DORA, the Thomas Murray Executive Readiness for DORA Workshops present an opportunity for executives and board members to understand the scope and implications of DORA for their organisations. This includes understanding your organisation's current exposure to regulatory enforcement and punitive actions for non-compliance.
Why Thomas Murray?
These services are the pillars of consulting excellence within Thomas Murray's cyber advisory practice. Our unified team of experts will support you as your needs evolve and your requirements grow.
We embed threat intelligence in all that we do and the language we speak. This ensures that you understand the relevance of our work and knowledge as they relate to the context of your business. We ensure that you are uniquely positioned to manage your cyber risk proactively.
Our team is relentlessly focused on helping our clients identify and manage cyber risk: we are responsive, dependable, and of the highest integrity, ensuring that value is realised. We put your needs at the centre of everything we do.